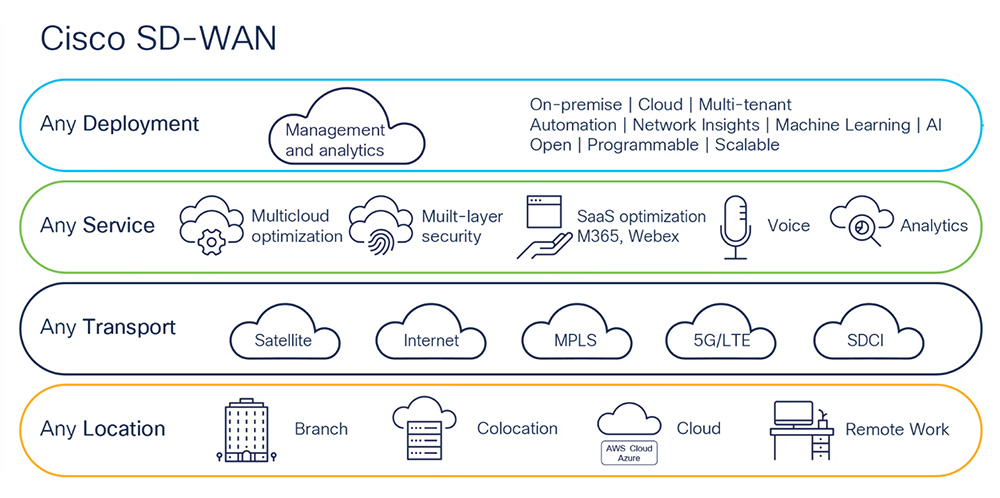
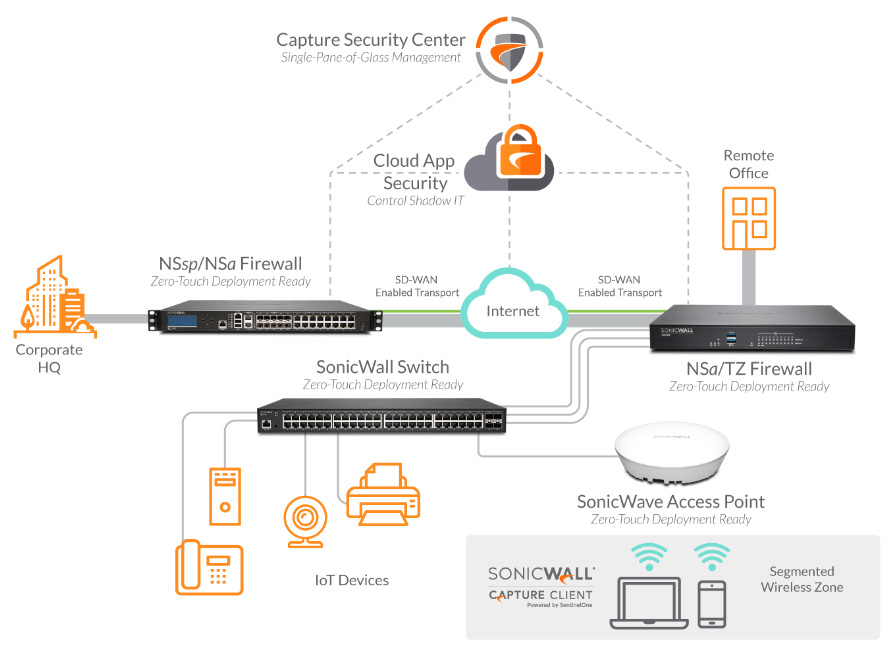
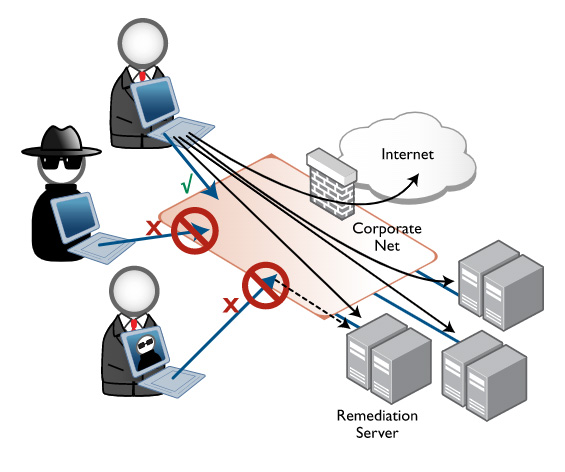
Cisco Secure Firewall – Turn Your Entire Network into An Extension of Your Security Architecture.

As our business-critical applications are a blend of cloud and on-premise based and users need secure access to resources from everywhere, the traditional firewall approach no longer works. Our single network perimeter has evolved to multiple micro-perimeters. For many organizations the application is the new perimeter, and traditional firewall deployments have evolved to a mixture of physical, virtual, and cloud-native appliances. As a result, organizations are struggling to operationalize support for modern application environments. The challenges of how to maintain consistent visibility, policy enforcement, and uniform threat visibility without opening vulnerabilities that expose the organization to risk.
Cisco, is building a network security vision, NetWORK, that enables a more agile, automated, and integrated approach for harmonizing policies and enforcement across modern dynamic applications and increasingly heterogenous networks. Secure Firewall gives you the deepest set of integrations between core networking functions and network security, delivering the most secure architecture ever. The result is a complete security portfolio that protects your applications and users everywhere.
Why Cisco?
The Cisco Secure Firewall portfolio delivers greater protections for your network against an increasingly evolving and complex set of threats. With Cisco, you’re investing in a foundation for security that is both agile and integrated- leading to the strongest security posture available today and tomorrow.
From your data center, branch offices, cloud environments, and everywhere in between, you can leverage the power of Cisco to turn your existing network infrastructure into an extension of your firewall solution, resulting in world class security controls everywhere you need them.
Investing in a Secure Firewall appliance today gives you robust protections against even the most sophisticated threats without compromising performance when inspecting encrypted traffic. Further, integrations with other Cisco and 3rd party solutions provides you with a broad and deep portfolio of security products, all working together to correlate previously disconnected events, eliminate noise, and stop threats faster.
Turn intent into action
Unify policy across your environment and prioritize what’s important. Having security resilience is about shoring up your architecture against threats and using automation to save time.
Achieve superior visibility
Regain visibility and control of your encrypted traffic and application environments. See more and detect more with Cisco Talos, while leveraging billions of signals across your infrastructure with security resilience.
Drive efficiency at scale
Only Secure Firewall includes license entitlement for SecureX, our open orchestration and XDR experience. The combination increases productivity across your teams and hybrid environments, while reducing threat dwell times.
Make zero trust practical
Secure Firewall makes a zero-trust posture achievable and cost-effective with network, microsegmentation, and app security integrations. Automate access and anticipate what comes next.