Capture Advanced Threat Protection (ATP)
SonicWall Capture ATP is a cloud-based, multi-engine sandbox that revolutionizes advanced threat detection. Included with Capture ATP, SonicWall’s patented Real-Time Deep Memory Inspection™ (RTDMI) blocks zero-day and unknown threats at the gateway — even those that hide via encryption or don’t exhibit malicious behavior.
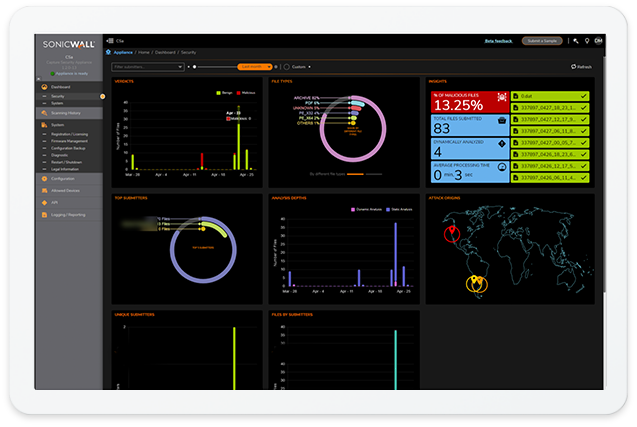
The Advanced Protection You Need, Where You Need It
SonicWall Capture ATP scans a broad range of file types to prevent zero-day attacks, targeted malware, advanced ransomware and more. Capture ATP analyzes behavior in a multi-engine sandbox platform that includes full system emulation, hypervisor-level analysis, virtualized sandboxing and RTDMI™, which uses real-time, memory-based inspection techniques to force malware to reveal its weaponry into memory.
By giving admins the ability to block until verdict, create customized policies and scan select files in the cloud, SonicWall Capture ATP combines the efficiency of automation with greater flexibility and control.
Superior Threat Prevention. Faster, More Accurate Verdicts.
SonicWall Capture ATP offers higher security effectiveness, faster response times and a lower total cost of ownership.

Stop Unknown Malware and Zero-Day Threats
Blocks malware, even if it’s hiding in encryption or not behaving maliciously.

Inspect More File Types
Supports analysis for PE, DLL, PDF, MS Office docs, archives, JAR and APK — plus multiple OSs.

Block Until Verdict
Potentially malicious files can be held at the gateway until an admin takes action.

Rapid Remediation
Files go from inspection to verdict within milliseconds, stopping follow-on attacks and ensuring a better user experience
Multi-Engine Sandbox
By combining multi-engine sandbox technology, system emulation and virtualization techniques, SonicWall Capture ATP detects more threats faster than single sandbox solutions.
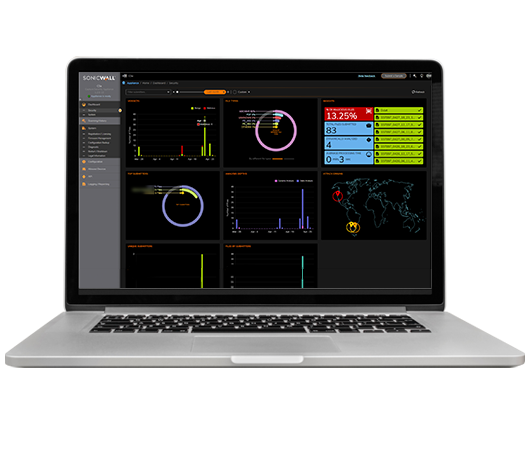
- The solution scans traffic and extracts suspicious code for analysis.
- Malware capabilities are replicated over various environments — all without detection.
- SonicWall Capture Labs rapidly deploys remediation signatures to SonicWall security products, so threats that fail anywhere fail everywhere.
Perfect Scores in Third-Party Testing
Independent ICSA Labs testing found SonicWall Capture ATP delivers better threat protection, with zero false positives, than competitors.
Multi-Engine Sandbox. Multi-Solution Flexibility.
Delivering unparalleled real-time threat detection and protection, the SonicWall Capture ATP service with RTDMI can be added to a variety of SonicWall’s latest security products:
Secure Remote Access
Connect and secure your growing remote workforce and devices.
Firewalls
Defend your physical networks from malware, intrusions and more with best-in-class protection.
Wireless Security
Enhance Wi-Fi security and performance with cloud-based deployment and management solutions.
Cloud App Security
Protect business-critical SaaS apps — including Microsoft Office 365, G Suite, Box and Dropbox — in real time.
Virtual Firewalls
Defend your business and data within virtual networks, for both public and private clouds.
Secure Email
Shield your organization from advanced email threats, including targeted phishing attacks, ransomware and BEC.
Resources:
- For more Information about this click here : https://www.sonicwall.com/products/capture-advanced-threat-protection/
- For more information about Sonicwall, Please visit: https://www.sysllc.com/product-category/sonicwall-partner-in-dubai-uae/
- To follow syscom page in Facebook:https://www.facebook.com/syscomuae/
- Check our latest updates in LinkedIn: https://www.linkedin.com/company/13588260/admin/
- To follow syscom page in Twitter: https://twitter.com/sysllcuae